Carbene: Difference between revisions
en>Octahedron80 No edit summary |
en>Mohamed CJ m →Structure and bonding: clean up using AWB |
||
| Line 1: | Line 1: | ||
[[File:Dangling Pointer.pdf|thumb|Dangling Pointer]] | |||
'''Dangling pointers''' and '''wild pointers''' in [[computer programming]] are [[data pointer|pointers]] that do not point to a valid object of the appropriate type. These are special cases of [[memory safety]] violations. | |||
Dangling pointers arise when an object is deleted or deallocated, without modifying the value of the pointer, so that the pointer still points to the memory location of the deallocated memory. As the system may reallocate the previously freed memory to another process, if the original program then [[dereference operator|dereferences]] the (now) dangling pointer, ''[[undefined behavior|unpredictable behavior]] may result'', as the memory may now contain completely different data. This is especially the case if the program writes data to memory pointed by a dangling pointer, a silent corruption of unrelated data may result, leading to subtle [[software bug|bugs]] that can be extremely difficult to find, or cause [[segmentation fault]]s (UNIX, Linux) or [[general protection fault]]s (Windows). If the overwritten data is bookkeeping data used by the system's memory allocator, the corruption can cause system instabilities. | |||
Wild pointers arise when a pointer is used prior to initialization to some known state, which is possible in some programming languages. They show the same erratic behaviour as dangling pointers, though they are less likely to stay undetected. | |||
==Cause of dangling pointers== | |||
In many languages (e.g., the [[C (programming language)|C programming language]]) deleting an object from memory explicitly or by destroying the stack frame on return does not alter associated pointers. The pointer still points to the same location in memory even though the reference has since been deleted and may now be used for other purposes. | |||
A straightforward example is shown below: | |||
<source lang="C"> | |||
{ | |||
char *dp = NULL; | |||
/* ... */ | |||
{ | |||
char c; | |||
dp = &c; | |||
} /* c falls out of scope */ | |||
/* dp is now a dangling pointer */ | |||
} | |||
</source> | |||
If the operating system is able to detect run-time references to [[null pointer]]s, a solution to the above is to assign 0 (null) to dp immediately before the inner block is exited. Another solution would be to somehow guarantee dp is not used again without further initialization. | |||
Another frequent source of dangling pointers is a jumbled combination of <tt>malloc()</tt> and <tt>free()</tt> library calls: a pointer becomes dangling when the block of memory it points to is freed. As with the previous example one way to avoid this is to make sure to reset the pointer to null after freeing its reference—as demonstrated below. | |||
<source lang="C"> | |||
#include <stdlib.h> | |||
void func() | |||
{ | |||
char *dp = malloc(A_CONST); | |||
/* ... */ | |||
free(dp); /* dp now becomes a dangling pointer */ | |||
dp = NULL; /* dp is no longer dangling */ | |||
/* ... */ | |||
} | |||
</source> | |||
An all too common misstep is returning addresses of a stack-allocated local variable: once a called function returns, the space for these variables gets deallocated and technically they have "garbage values". | |||
<source lang="C"> | |||
int *func(void) | |||
{ | |||
int num = 1234; | |||
/* ... */ | |||
return # | |||
} | |||
</source> | |||
Attempts to read from the pointer may still return the correct value (1234) for a while after calling <tt>func</tt>, but any functions called thereafter will overwrite the stack storage allocated for <tt>num</tt> with other values and the pointer would no longer work correctly. If a pointer to <tt>num</tt> must be returned, <tt>num</tt> must have scope beyond the function—it might be declared as <tt>[[static variable|static]]</tt>. | |||
==Manual deallocation without dangling reference== | |||
Antoni Kreczmar (1945-1996) has created a complete object management system which is free of dangling reference phenomenon. | |||
See <ref>Gianna Cioni, Antoni Kreczmar, ''Programmed deallocation without dangling reference'', Information Processing Letters, v. 18, '''1984''', pp.179-185</ref> | |||
::: Scheme of axioms of the operation kill | |||
:::: Let x<sub>1</sub>, ... ,x<sub>n</sub> be variables, n > 0, 1≤i≤n. Each formula of the following scheme is a theorem of running system of Kreczmar. | |||
::::: <math>\color{blue} (x_1=\dots=x_n\neq none)\Rightarrow[kill(x_i)](x_1=\dots=x_n= none)\;\color{black}</math> | |||
::: ''<small>read as</small>'': if an object '' o '' is the value of ''n'' variables, then after execution of instruction ''kill(x<sub>i</sub>)'' the common value of these variables is ''none'' (it means that the object is from now unreachable and may be by the same operation kill deleted without any harm). Consequently: | |||
::::* there is no need to repeat the operation kill(x<sub>1</sub>),kill(x<sub>2</sub>), ... | |||
::::* there is no phenomenon of [[dangling reference]], | |||
::::* each attempt to access an attribute of the deleted object will be detected and signalized as an exception „''reference to none''”. | |||
Note: the cost of kill is constant O(1). | |||
==Cause of wild pointers== | |||
Wild pointers are created by omitting necessary initialization prior to first use. Thus, strictly speaking, every pointer in programming languages which do not enforce initialization begins as a wild pointer. | |||
This most often occurs due to jumping over the initialization, not by omitting it. Most compilers are able to warn about this. | |||
<source lang="C"> | |||
int f(int i) | |||
{ | |||
char *dp; /* dp is a wild pointer */ | |||
static char *scp; /* scp is not a wild pointer: | |||
* static variables are initialized to 0 | |||
* at start and retain their values from | |||
* the last call afterwards. | |||
* Using this feature may be considered bad | |||
* style if not commented */ | |||
} | |||
</source> | |||
==Security holes involving dangling pointers== | |||
Like [[buffer overflow|buffer-overflow]] bugs, dangling/wild pointer bugs frequently become security holes. For example, if the pointer is used to make a [[virtual function]] call, a different address (possibly pointing at exploit code) may be called due to the [[vtable]] pointer being overwritten. Alternatively, if the pointer is used for writing to memory, some other data structure may be corrupted. Even if the memory is only read once the pointer becomes dangling, it can lead to information leaks (if interesting data is put in the next structure allocated there) or to [[privilege escalation]] (if the now-invalid memory is used in security checks). | |||
==Avoiding dangling pointer errors== | |||
In C/C++, the simplest technique is to implement an alternative version of the <tt>free()</tt> (or alike) function or <tt>delete</tt> destructor which guarantees the reset of the pointer. However, this technique will not clear other pointer variables which may contain a copy of the pointer. | |||
<source lang="C"> | |||
#include <assert.h> | |||
#include <stdlib.h> | |||
/* Alternative version for 'free()' */ | |||
void safefree(void **pp) | |||
{ | |||
/* in debug mode, abort if pp is NULL */ | |||
assert(pp); | |||
if (pp != NULL) { /* safety check */ | |||
free(*pp); /* deallocate chunk, note that free(NULL) is valid */ | |||
*pp = NULL; /* reset original pointer */ | |||
} | |||
} | |||
int f(int i) | |||
{ | |||
char *p = NULL, *p2; | |||
p = (char *)malloc(1000); /* get a chunk */ | |||
p2 = p; /* copy the pointer */ | |||
/* use the chunk here */ | |||
safefree((void **)&p); /* safety freeing; does not affect p2 variable */ | |||
safefree((void **)&p); /* this second call won't fail */ | |||
char c = *p2; /* p2 is still a dangling pointer, so this is undefined behavior. */ | |||
return i + c; | |||
} | |||
</source> | |||
The alternative version can be used even to guarantee the validity of an empty pointer before calling <tt>malloc()</tt>: | |||
<source lang="C"> | |||
safefree(&p); /* i'm not sure if chunk has been released */ | |||
p = malloc(1000); /* allocate now */ | |||
</source> | |||
These uses can be masked through <tt>#define</tt> directives to construct useful macros, creating something like a metalanguage or can be embedded into a tool library apart. In every case, programmers using this technique should use the safe versions in every instance where <tt>free()</tt> would be used; failing in doing so leads again to the problem. Also, this solution is limited to the scope of a single program or project, and should be properly documented. | |||
Among more structured solutions, a popular technique to avoid dangling pointers is to use [[smart pointer]]s. A smart pointer typically uses [[reference counting]] to reclaim objects. Some other techniques include the [[tombstone (programming)|tombstones]] method and the [[locks-and-keys]] method. | |||
Another approach is to use the [[Boehm garbage collector]], a conservative [[garbage collection (computer science)|garbage collector]] that replaces standard memory allocation functions in C and [[C++]] with a garbage collector. This approach completely eliminates dangling pointer errors by disabling frees, and reclaiming objects by garbage collection. | |||
In languages like Java, dangling pointers cannot occur because there is no mechanism to explicitly deallocate memory. Rather, the garbage collector may deallocate memory, but only when the object is no longer reachable from any references. | |||
==Dangling pointer detection== | |||
To expose dangling pointer errors, one common programming technique is to set pointers to the [[null pointer]] or to an invalid address once the storage they point to has been released. When the null pointer is dereferenced (in most languages) the program will immediately terminate—there is no potential for data corruption or unpredictable behavior. This makes the underlying programming mistake easier to find and resolve. This technique does not help when there are multiple copies of the pointer. | |||
Some debuggers will automatically overwrite and destroy data that has been freed, usually with a specific pattern, such as <code>[[0xDEADBEEF]]</code> (Microsoft's Visual C/C++ debugger, for example, uses <code>0xCC</code>, <code>0xCD</code> or <code>0xDD</code> depending on what has been freed<ref>[http://msdn2.microsoft.com/en-us/library/aa270812(VS.60).aspx Visual C++ 6.0 memory-fill patterns]</ref>). This usually prevents the data from being reused by making it useless and also very prominent (the pattern serves to show the programmer that the memory has already been freed). | |||
Tools such as [[Polyspace]], [[TotalView]], [[Valgrind]], Mudflap,<ref>[http://gcc.gnu.org/wiki/Mudflap_Pointer_Debugging Mudflap Pointer Debugging]</ref> [[AddressSanitizer]], or tools based on [[LLVM]]<ref>Dhurjati, D. and Adve, V. [http://llvm.org/pubs/2006-DSN-DanglingPointers.pdf Efficiently Detecting All Dangling Pointer Uses in Production Servers]</ref> can also be used to detect uses of dangling pointers. | |||
Other tools ([http://www.cis.upenn.edu/acg/softbound/ SoftBound] and [http://www.semanticdesigns.com/Products/MemorySafety CheckPointer]) instrument the source code to collect and track legitimate values for pointers ("metadata") and check each pointer access against the metadata for validity. | |||
Another strategy, when suspecting a small set of classes, is to temporarily make all their member functions '''[[Virtual method|virtual]]''': after the class instance has been destructed/freed, its pointer to the [[Virtual method table|Virtual Method Table]] is set to <code>NULL</code>, and any call to a member function will crash the program and it will show the guilty code in the debugger. | |||
== Other uses == | |||
The term ''dangling pointer'' may also be used in contexts other than programming, especially by technical people. For example, a phone number for a person who has since changed phones is a real-world example of a dangling pointer.<ref>{{cite web |url=http://www.catb.org/jargon/html/D/dangling-pointer.html |accessdate=2014-01-07 |title=The Jargon File |section=dangling pointer |version=version 4.4.7}}</ref> Another example is an entry in an [[online encyclopedia]] that refers to another entry whose titled has been changed, changing any previously existing references to that entry into dangling pointers. | |||
==See also== | |||
{{Portal|Software Testing}} | |||
*[[Wild branch]] | |||
==References== | |||
{{reflist}} | |||
{{Memory management navbox}} | |||
{{DEFAULTSORT:Dangling Pointer}} | |||
[[Category:Software bugs]] | |||
[[Category:Computer security exploits]] | |||
Revision as of 11:36, 31 January 2014
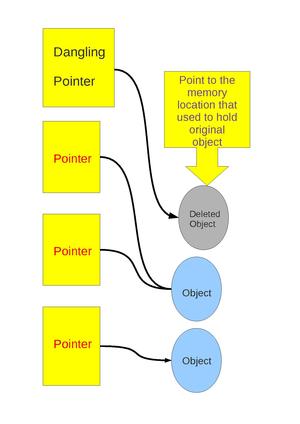
Dangling pointers and wild pointers in computer programming are pointers that do not point to a valid object of the appropriate type. These are special cases of memory safety violations.
Dangling pointers arise when an object is deleted or deallocated, without modifying the value of the pointer, so that the pointer still points to the memory location of the deallocated memory. As the system may reallocate the previously freed memory to another process, if the original program then dereferences the (now) dangling pointer, unpredictable behavior may result, as the memory may now contain completely different data. This is especially the case if the program writes data to memory pointed by a dangling pointer, a silent corruption of unrelated data may result, leading to subtle bugs that can be extremely difficult to find, or cause segmentation faults (UNIX, Linux) or general protection faults (Windows). If the overwritten data is bookkeeping data used by the system's memory allocator, the corruption can cause system instabilities.
Wild pointers arise when a pointer is used prior to initialization to some known state, which is possible in some programming languages. They show the same erratic behaviour as dangling pointers, though they are less likely to stay undetected.
Cause of dangling pointers
In many languages (e.g., the C programming language) deleting an object from memory explicitly or by destroying the stack frame on return does not alter associated pointers. The pointer still points to the same location in memory even though the reference has since been deleted and may now be used for other purposes.
A straightforward example is shown below:
{
char *dp = NULL;
/* ... */
{
char c;
dp = &c;
} /* c falls out of scope */
/* dp is now a dangling pointer */
}
If the operating system is able to detect run-time references to null pointers, a solution to the above is to assign 0 (null) to dp immediately before the inner block is exited. Another solution would be to somehow guarantee dp is not used again without further initialization.
Another frequent source of dangling pointers is a jumbled combination of malloc() and free() library calls: a pointer becomes dangling when the block of memory it points to is freed. As with the previous example one way to avoid this is to make sure to reset the pointer to null after freeing its reference—as demonstrated below.
#include <stdlib.h>
void func()
{
char *dp = malloc(A_CONST);
/* ... */
free(dp); /* dp now becomes a dangling pointer */
dp = NULL; /* dp is no longer dangling */
/* ... */
}
An all too common misstep is returning addresses of a stack-allocated local variable: once a called function returns, the space for these variables gets deallocated and technically they have "garbage values".
int *func(void)
{
int num = 1234;
/* ... */
return #
}
Attempts to read from the pointer may still return the correct value (1234) for a while after calling func, but any functions called thereafter will overwrite the stack storage allocated for num with other values and the pointer would no longer work correctly. If a pointer to num must be returned, num must have scope beyond the function—it might be declared as static.
Manual deallocation without dangling reference
Antoni Kreczmar (1945-1996) has created a complete object management system which is free of dangling reference phenomenon. See [1]
- Scheme of axioms of the operation kill
- read as: if an object o is the value of n variables, then after execution of instruction kill(xi) the common value of these variables is none (it means that the object is from now unreachable and may be by the same operation kill deleted without any harm). Consequently:
- there is no need to repeat the operation kill(x1),kill(x2), ...
- there is no phenomenon of dangling reference,
- each attempt to access an attribute of the deleted object will be detected and signalized as an exception „reference to none”.
Note: the cost of kill is constant O(1).
Cause of wild pointers
Wild pointers are created by omitting necessary initialization prior to first use. Thus, strictly speaking, every pointer in programming languages which do not enforce initialization begins as a wild pointer.
This most often occurs due to jumping over the initialization, not by omitting it. Most compilers are able to warn about this.
int f(int i)
{
char *dp; /* dp is a wild pointer */
static char *scp; /* scp is not a wild pointer:
* static variables are initialized to 0
* at start and retain their values from
* the last call afterwards.
* Using this feature may be considered bad
* style if not commented */
}
Security holes involving dangling pointers
Like buffer-overflow bugs, dangling/wild pointer bugs frequently become security holes. For example, if the pointer is used to make a virtual function call, a different address (possibly pointing at exploit code) may be called due to the vtable pointer being overwritten. Alternatively, if the pointer is used for writing to memory, some other data structure may be corrupted. Even if the memory is only read once the pointer becomes dangling, it can lead to information leaks (if interesting data is put in the next structure allocated there) or to privilege escalation (if the now-invalid memory is used in security checks).
Avoiding dangling pointer errors
In C/C++, the simplest technique is to implement an alternative version of the free() (or alike) function or delete destructor which guarantees the reset of the pointer. However, this technique will not clear other pointer variables which may contain a copy of the pointer.
#include <assert.h>
#include <stdlib.h>
/* Alternative version for 'free()' */
void safefree(void **pp)
{
/* in debug mode, abort if pp is NULL */
assert(pp);
if (pp != NULL) { /* safety check */
free(*pp); /* deallocate chunk, note that free(NULL) is valid */
*pp = NULL; /* reset original pointer */
}
}
int f(int i)
{
char *p = NULL, *p2;
p = (char *)malloc(1000); /* get a chunk */
p2 = p; /* copy the pointer */
/* use the chunk here */
safefree((void **)&p); /* safety freeing; does not affect p2 variable */
safefree((void **)&p); /* this second call won't fail */
char c = *p2; /* p2 is still a dangling pointer, so this is undefined behavior. */
return i + c;
}
The alternative version can be used even to guarantee the validity of an empty pointer before calling malloc():
safefree(&p); /* i'm not sure if chunk has been released */
p = malloc(1000); /* allocate now */
These uses can be masked through #define directives to construct useful macros, creating something like a metalanguage or can be embedded into a tool library apart. In every case, programmers using this technique should use the safe versions in every instance where free() would be used; failing in doing so leads again to the problem. Also, this solution is limited to the scope of a single program or project, and should be properly documented.
Among more structured solutions, a popular technique to avoid dangling pointers is to use smart pointers. A smart pointer typically uses reference counting to reclaim objects. Some other techniques include the tombstones method and the locks-and-keys method.
Another approach is to use the Boehm garbage collector, a conservative garbage collector that replaces standard memory allocation functions in C and C++ with a garbage collector. This approach completely eliminates dangling pointer errors by disabling frees, and reclaiming objects by garbage collection.
In languages like Java, dangling pointers cannot occur because there is no mechanism to explicitly deallocate memory. Rather, the garbage collector may deallocate memory, but only when the object is no longer reachable from any references.
Dangling pointer detection
To expose dangling pointer errors, one common programming technique is to set pointers to the null pointer or to an invalid address once the storage they point to has been released. When the null pointer is dereferenced (in most languages) the program will immediately terminate—there is no potential for data corruption or unpredictable behavior. This makes the underlying programming mistake easier to find and resolve. This technique does not help when there are multiple copies of the pointer.
Some debuggers will automatically overwrite and destroy data that has been freed, usually with a specific pattern, such as 0xDEADBEEF (Microsoft's Visual C/C++ debugger, for example, uses 0xCC, 0xCD or 0xDD depending on what has been freed[2]). This usually prevents the data from being reused by making it useless and also very prominent (the pattern serves to show the programmer that the memory has already been freed).
Tools such as Polyspace, TotalView, Valgrind, Mudflap,[3] AddressSanitizer, or tools based on LLVM[4] can also be used to detect uses of dangling pointers.
Other tools (SoftBound and CheckPointer) instrument the source code to collect and track legitimate values for pointers ("metadata") and check each pointer access against the metadata for validity.
Another strategy, when suspecting a small set of classes, is to temporarily make all their member functions virtual: after the class instance has been destructed/freed, its pointer to the Virtual Method Table is set to NULL, and any call to a member function will crash the program and it will show the guilty code in the debugger.
Other uses
The term dangling pointer may also be used in contexts other than programming, especially by technical people. For example, a phone number for a person who has since changed phones is a real-world example of a dangling pointer.[5] Another example is an entry in an online encyclopedia that refers to another entry whose titled has been changed, changing any previously existing references to that entry into dangling pointers.
See also
Sportspersons Hyslop from Nicolet, usually spends time with pastimes for example martial arts, property developers condominium in singapore singapore and hot rods. Maintains a trip site and has lots to write about after touring Gulf of Porto: Calanche of Piana.
References
43 year old Petroleum Engineer Harry from Deep River, usually spends time with hobbies and interests like renting movies, property developers in singapore new condominium and vehicle racing. Constantly enjoys going to destinations like Camino Real de Tierra Adentro.
Template:Memory management navbox
- ↑ Gianna Cioni, Antoni Kreczmar, Programmed deallocation without dangling reference, Information Processing Letters, v. 18, 1984, pp.179-185
- ↑ Visual C++ 6.0 memory-fill patterns
- ↑ Mudflap Pointer Debugging
- ↑ Dhurjati, D. and Adve, V. Efficiently Detecting All Dangling Pointer Uses in Production Servers
- ↑ Template:Cite web
\;\color {black}](https://wikimedia.org/api/rest_v1/media/math/render/svg/65167df9cc83ffa15204ff743ef79d16e6b96337)